Getting to know your network traffic and its patterns can you save hours in troubleshooting, network capacity planning, or security analysis. Information such as, who are the top talkers on the network, what protocols are they using, and the top destinations are key into a successful network monitoring.
Thankfully, Netflow makes all of that more comfortable.
What is Netflow?
Netflow is a network protocol that collects information about all the traffic running through a Netflow-enabled device, records traffic data, and helps discover traffic patterns.
Network admins have many reasons for using Netflow. They use it to ensure and improve security by knowing the baseline of where the traffic is and its inconsistencies. An admin can also use it to learn how traffic patterns look like before adding a new device or application. With Netflow, an admin can create billing reports based on bandwidth usage.
What is the Origin of Netflow?
Netflow was initially developed by and for Cisco switching technologies around 1996, since the release of IOS 11.1. Cisco networking devices series 7000, 7200, and 7500 implemented Netflow for the first time.
Now, other networking vendors have added their version of Netflow, such as j-Flow by Juniper, sFlow by HP, NetStream by Huawei, and RFlow by Ericsson.
The latest version of this protocol is Netflow Version 9. There is a NetFlow v10, referred to as IPFIX which is not considered Netflow but a variance. Still, IPFIX is very similar to Netflow v9 process and structure.
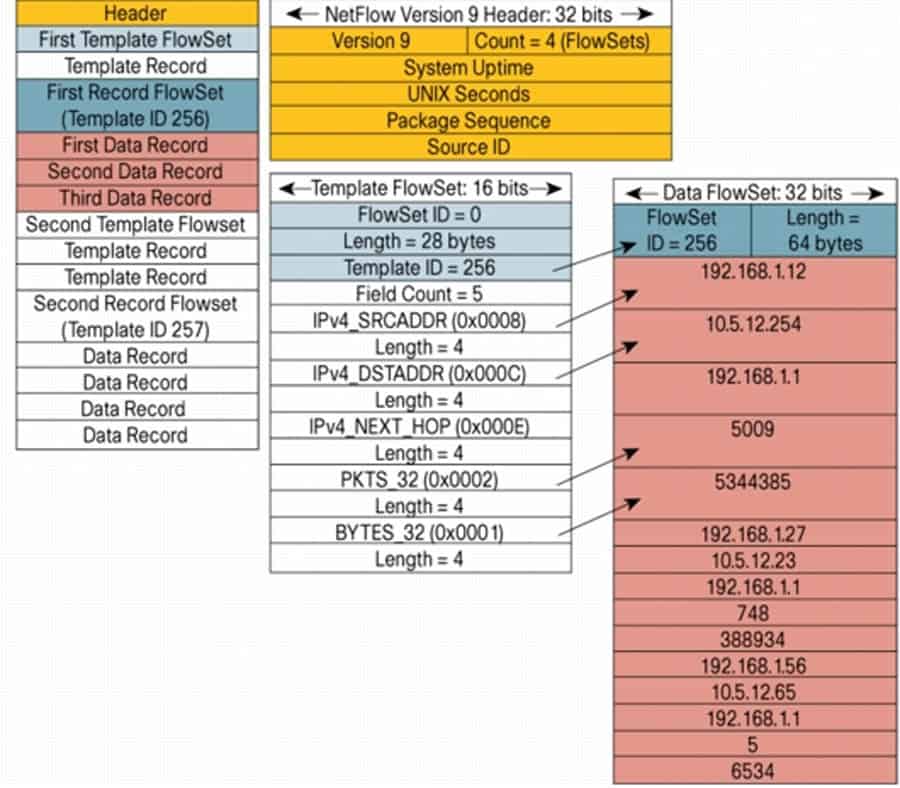
The following is a NetFlow V9 export packet example:
What Information can Netflow obtain?
To be able to obtain traffic information, the NetFlow V9 data communication frames carry a vast arrange of information. The Field Type in the data frame of a NetFlow packet contains information such as (but not limited to):
- Number of Flows.
- IP Protocol.
- Type of Service.
- TCP/UDP source and destination port.
- IPv4/IPv6 source and destination.
- BGP Autonomous System.
- MPLS TOP.
- MAC source and destination.
- Min and Max Time-To-Live.
With this information, Netflow allows devices to create a record for each traffic flow. The device sends these records to a Netflow collector, which analyzes the data and reports statistics (top talkers, top protocols, etc.).
Netflow Components
As mentioned earlier, Netflow is a Protocol that Collects Flow Data from the network traffic and forwards it to a collector.The Netflow collector, which consolidates all data, receives the record from the exporter (as shown in the picture below).
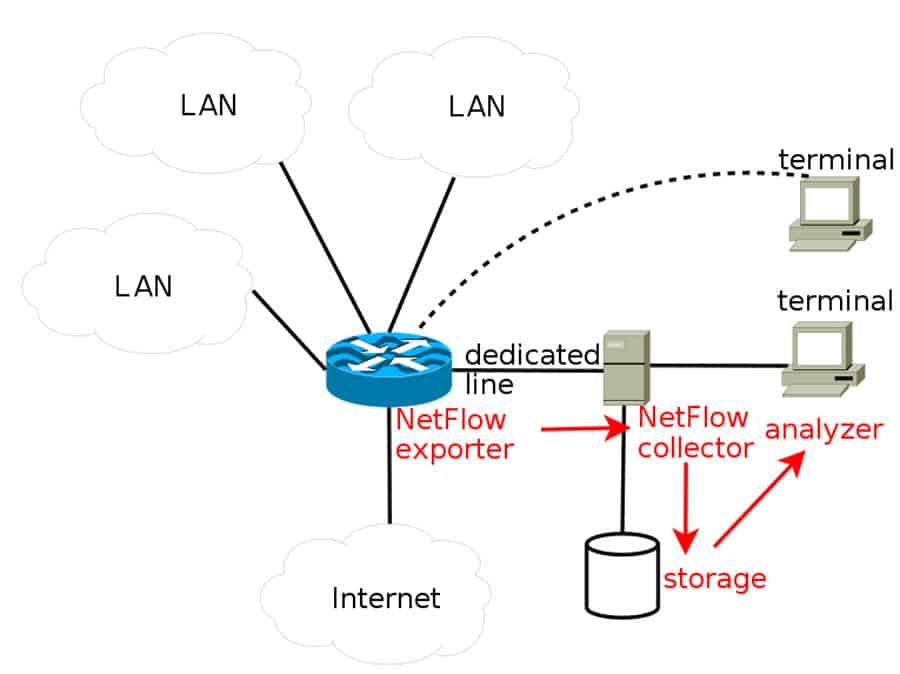
Three fundamental elements usually referred to as Netflow Collector, Exporter, and the Analyzer, play an essential role in Netflow. Their ultimate job is to organize the flow data together into a readable format so that the network admin can analyze (using applications) and make some sense out of the data.
- NetFlow Exporter:
Sends out monitored flows of traffic. The Exporter keeps track of the traffic packets going in and out and creates records. It sends these records to one or more collectors. - NetFlow Collector:
It gathers and stores all records sent from an exporter, then sends them to the analyzer. It can save them locally or through external storage. - NetFlow Analyzer:
It is usually an application that can analyze all records and look for specific information, such as bandwidth usage, intrusion detection, etc. It converts them into beautiful graphs and reports to reflect what is happening on the network.
The Netflow records are usually sent using a UDP and received by a collector. The destination UDP port and IP of the collector must be specified on the Netflow Exporter. Although the RFC 3954 does not determine any Netflow UDP port number, common values used by Cisco are ports 2055, 9555 or 9995, 9025, or 9026.
Netflow vs SNMP
Traditionally, network admins relied entirely on SNMP to monitor traffic and bandwidth.
SNMP “Simple Network Management Protocol” is a standard that helps different devices on the network share information. It is used to manage and keep track of network devices and their performance. SNMP is recommended for every day monitoring situations, such as bandwidth utilization, CPU loads, or interface status, and many other parameters.
Although SNMP is also an excellent tool for capacity planning, it doesn’t help much when identifying traffic patterns and their applications.
Netflow also provides a means to monitor a network, but it uses an entirely different method than SNMP. The following table shows the fundamental functionality differences.
| SNMP | Netflow | |
| Collection Model | MIB Counters | TCP/UDP/ICMP flow Records |
| Amount of Information | Small | Medium (Depending on sampling conditions) |
| Collecting Information | Data collected from the interface. | From layer 2 – 4 |
| Mode | Pull | Push |
| RFC | RFC3411 | RFC3954 |
Some of the most significant differences between Netflow vs SNMP are:
- NetFlow is a more compact solution for monitoring than SNMP. When Cisco designed Netflow, they were developing a lighter solution than SNMP. Netflow can scale better when it comes to collecting performance measurements in IP networks.
- Netflow is used for network traffic collection, analysis, and monitoring. SNMP is preferred for traditional network monitoring. It offers a simple way of gathering bandwidth and network utilization data.
- Netflow delivers more granular information on bandwidth usage. It tells you who is consuming the most bandwidth and with what application. But it is not designed to collect parameters such as CPU and memory loads, as SNMP does.
Netflow vs. PCAP
Pcap (packet capture) is a protocol used for capturing network traffic. Unix systems implement a pcap in a library called libpcap. There is also a Windows libpcap port called WinPcap. These pcap libraries provide packet capture, saving, reading, and filter engines for many network monitoring tools.
Some applications are written using pcap libraries (libpcap, Winpcap, or Npcap), to be able to capture traffic and analyze it, some examples are Wireshark and tcpdump.
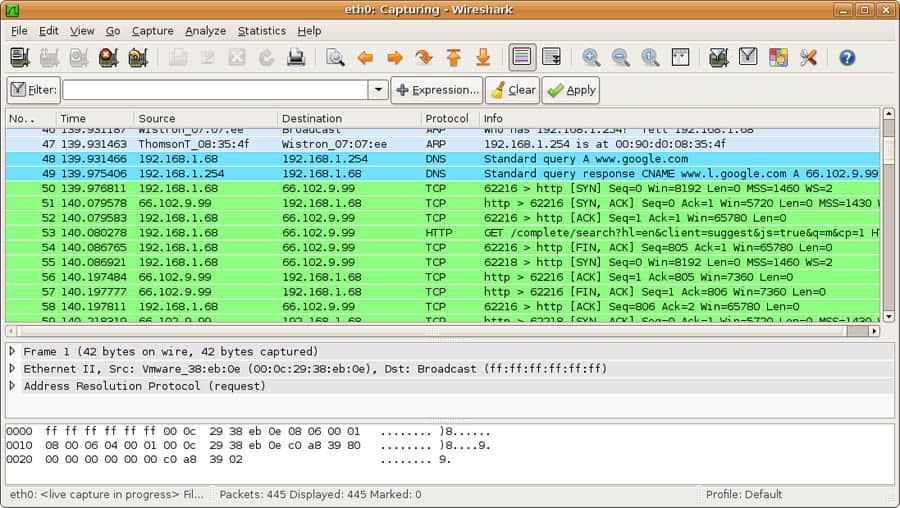
Wireshark is considered a packet capture software that relies entirely on pcap. It captures traffic packets and analyzes them precisely as how they look on transmission.
Below is a screenshot of Wireshark in action.
What are the main differences between a pcap software (such as Wireshark) and Netflow?
- Netflow is used for statistics. Netflow shows statistics about the collected network flows based on the traffic patterns previously defined. It does not capture packets, only shows flows. Wireshark is used for deep analytics, because it captures packets as they come, including their payload.
- Netflow is a summary of the information. It doesn’t take too much storage space. With Netflow, historical and real-time data can be accessed fast. Pcap, on the other hand, collects too much data over a short period. It captures full packets that tell the entire story.
The following chart shows their difference in functionalities.
| libpcap (Wireshark) | Netflow | |
| Model | Packet Capture | TCP/UDP/ICMP flow records |
| Amount of Information | Large | Medium (Depending on sampling conditions) |
| View Information | Non-sampled. View payload | Generally sampled. |
| Collecting Information | Data collected from the interface. | From layer 2 – 4 |
| License | Open source | Cisco license |
Thanks to their differences, Netflow and pcap are best when used together. They are frequently used as a killer combination for network forensics and general troubleshooting.
Netflow gives you an efficient and quick monitoring solution, so network admins can be updated when something changes. But having access to full packets with Wireshark (or other pcap solution), give admins access to the whole communication process.
Netflow shows quick statistics, and Wireshark shows in-depth analysis.
Netflow vs sFlow
sFlow stands for sampled Flow and is used for exporting packets at the data link layer. It is a stateless packet sampling protocol designed for fast monitoring samplings. sFlow can provide statistics on different protocols from Layer 2 to Layer 7 of the OSI model.
The main differences between Netflow and sFlow regarding functionality as explained in the chart below,
| sFlow | Netflow | |
| Model | Packet-based | Flow-based |
| Sampling | Large, 1 – 1000s. Depending on configuration. | Medium, 1 – 32. Depending on configuration. |
| Collecting information | Full layer 2–7 visibility | From layer 2 – 4 |
| RFC | RFC3176 | RFC3954 |
The main differences between Netflow and sFlow are:
- sFlow is not dependent on IP. Netflow v9 can only sample based on IP, MPLS, or BGP. Whereas sFlow can sample everything from Layer 2 to 7.
- sFlow is designed for high-speed network monitoring. sFlow does not keep a flow cache at the exporting device, so its sampling is much faster than Netflow.
- sFlow is more scalable than Netflow. Netflow collects flows in a device, but as the traffic increases, it becomes more difficult to manage every flow. Sampling on sFlow can be much faster, so there are fewer chances of losing valuable information.
The Evolution of Netflow and What is Next?
There is a high chance that we’ll continue using Netflow, SNMP, pcap, sFlow, and other protocols to watch our network traffic.
But the network traffic monitoring technologies have been evolving dramatically — from Netflow, sFlow, IPFIX, and now Huawei’s NetStream. Another significant variation of Netflow is Flexible Netflow (FnF) which is an extension to NetFlow v9.
We’ll probably stop using some old protocols and improve others.
For example, IPFIX and FnF allow different vendor IDs to be placed in their identifier, allowing to capture and collect any data, probably more than SNMP. When these technologies are improved, we’ll probably see less of SNMP around.