The Monitoring and Management of firewalls, intrusion detection systems (IDSes) and Virtual Private Networks (VPNs) are some of the most common managed security services.
These services can be simple or complex. A managed firewall service may begin and end with the purchase and installation of a perimeter firewall that protects the client’s systems and networks that have a connection to the Internet.
A managed firewall service may also expand to include deployment on internal sub-networks with differing access policies, regular configuration and rule set updates, monitoring, intrusion detection, intrusion response, and replacing older firewall technology with new technology.
Similarly, IDS services may be limited to the purchase and installation of an initial, single sensor capability to detect and report intrusions; or they may address full life-cycle management that incorporates analysis across multiple sensors.
An IDS service can be deployed both on internal sub-networks and those connected to the Internet.
A managed VPN service can be provided at varying levels to ensure secure remote access across a small or large user population with differing authentication requirements and authorization rights.
Managed Firewall/IDS/VPN Service
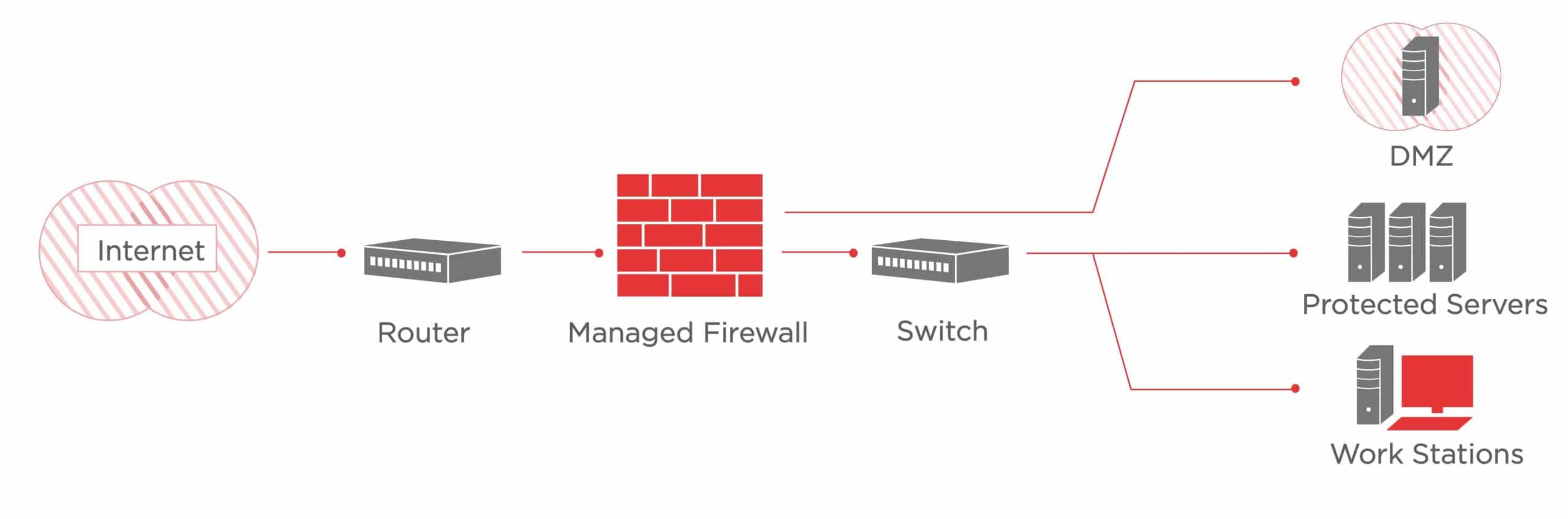
via axiatp.com
A managed firewall/IDS/VPN service can include a narrow or wide range of features, service levels and capabilities. The client needs to determine the requirements for each feature, service level, and capability in order to meet business objectives and protect critical assets.
The client and provider need to mutually determine roles and responsibilities including who makes service decisions and choices. In some cases, the client will make the decisions, but when it comes to choosing features of the service, the provider is often more knowledgeable and is therefore in the best position to make the right decision.
A provider may own and install the firewall/IDS/VPN that is used to protect the client’s perimeter or internal sub-networks.
The client avoids the cost of the security system (hardware and software) but may pay more for the recurring costs (such as 3M – Monitoring, Management and Maintenance).
Service Description
The client should also request a Detailed Description of Security Services including:
- Initial analysis, design, and implementation (to include transition and production operation);
- Ongoing reassessment of the firewall configuration and infrastructure to ensure that the current deployment reflects policy and requirements;
- Any services available to assist the client with implementing initial firewall policies;
- Managed IDS services including initial architecture analysis, design, implementation (to include transition and production operation), and ongoing reassessment of the IDS infrastructure;
- Deployment of IDS and fine-tuning the signatures to ensure it detects what it is supposed to. Customization of signatures to suite the client’s environment is required;
- Monitoring, analyzing and reporting of security system log results (usage, attack attempts blocked, intrusion detections, summaries, etc.); and
- Service level features, such as adding new firewall rules, modifying a currently executing rule, and fine-tuning/customising IDS signatures along with any limits on how often each feature can be requested and the response times for a given feature.




